St. Jude Medical May Not Have a Cybersecurity Problem After All
August 31, 2016
Error alerts triggered by simulated attack are actually what show up when the St. Jude cardio device isn't plugged in, researchers say.
Nancy Crotti
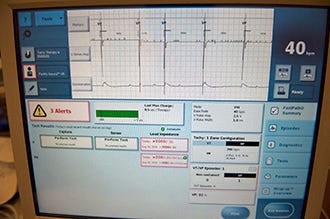 University of Michigan researchers have shot some holes into allegations that St. Jude Medical cardiac devices are vulnerable to cyberattacks.
University of Michigan researchers have shot some holes into allegations that St. Jude Medical cardiac devices are vulnerable to cyberattacks.
The researchers reproduced experiments that led to the allegations and came to "strikingly different conclusions," according to a report from the university.
Short-selling investment firm Muddy Waters Capital LLC and medtech security firm MedSec Ltd. made the allegations of security flaws in a host of St. Jude cardiac devices last week, prompting a swift denial from St. Jude even as the Minnesota-based company took a hit on its stock price.
Then Muddy Waters posted a video that it claims shows the hacking of a St. Jude pacemaker. St. Jude said the video showed a safety feature, not a flaw, and demonstrated "their fundamental lack of understanding" of the company's technology.
St. Jude said its devices are designed to go into a "safe" mode if unexpected conditions are detected, in which the pre-programmed pacing and defibrillation functions of the devices revert to safe settings. Some devices disable further radio frequency communications for a period of time, "which may appear to the untrained eye as having rendered the device disabled, although it continues to function," the company said in a statement.
Now come the Michigan researchers, who say the error messages that Muddy Waters cites as evidence of a successful "crash attack" into a home-monitored implantable cardiac defibrillator are actually the error alerts that display if the device isn't properly plugged in. The research team includes several leading medical device security researchers and a cardiologist from the the university health system's Frankel Cardiovascular Center.
"We're not saying the report is false. We're saying it's inconclusive because the evidence does not support their conclusions. We were able to generate the reported conditions without there being a security issue," said Kevin Fu, an associate professor of computer science and engineering and director of the Archimedes Center for Medical Device Security at the university. Fu is also co-founder of medical device security startup Virta Labs.
The Michigan team used a new, properly functioning model of the defibrillator that the Muddy Waters study used--the Fortify Assura VR. In several additional instances, they say the device operated properly, but they didn't go as far as to declare the St. Jude devices or any others completely secure.
A defibrillator's electrodes are connected to heart tissue by wires that are woven through blood vessels. The wires enable implantable defibrillators to perform sensing operations and send shocks if necessary.
"When these wires are disconnected, the device generates a series of error messages: two indicate high impedance, and a third indicates that the (device) is interfering with itself," said Denis Foo Kune, a former university postdoctoral researcher and co-founder of Virta Labs.
Muddy Waters claims these error messages are proof of a security breach, but the Michigan researchers said they believe the device is acting correctly.
"To the armchair engineer it may look startling, but to a clinician it just means you didn't plug it in," Fu said in the university statement. "In layman's terms, it's like claiming that hackers took over your computer, but then later discovering that you simply forgot to plug in your keyboard."
The dustup occurs as St. Jude prepares for a $25 billion takeover by Abbott Laboratories. An Abbott spokeswoman said in an email that the company continues to "collaborate with St. Jude to advance the transaction."
Nancy Crotti is a contributor to Qmed.
Like what you're reading? Subscribe to our daily e-newsletter.
[Image courtesy of University of Michigan]
About the Author(s)
You May Also Like


