June 18, 2015
Medical devices could be the weakest link in the medical industry security chain.
Alan Grau
The HIPPA data privacy act of 1996 made patient privacy and data security a top priority for the medical industry. Despite this, medical data breaches continue to make headlines and hackers continue to find ways to steal patient data. Health insurance credentials can be worth twenty times the value of a credit card on the black market making medical data a lucrative target.
Cyber criminals are successfully searching for and finding weak links in the medical industry security chain. The recent MedJack report from TrapX security shows that it is medical devices that are often that weakest link.
The report provides details of criminals hijacking medical devices and using the compromised devices to launch broader attacks against the hospital's "secure" networks. The security of many medical devices is weak, making them easy targets. Once compromised, they were able to remain undetected for a significant period of time, using the hijacked devices to gain access further into the network, discover medical records, and finally to exfiltrate the medical record data. The report details attacks on:
blood Gas Analyzers (BGA) in a hospital laboratory.
picture Archive and Communications System (PACS) a hospital radiology department.
x-ray equipment.
|
By using a variety of cyber defense modes, Icon Labs' Floodgate is designed to protect medical systems and equipment against cyber-attack. |
Keeping Pace with Cyber-Attacks
Many of the medical devices currently in use are based on designs that predated the pervasive cyber-threats that we see today. Fifteen or twenty years ago, devices were not being connected to a world-wide network of computers that anyone could access. Medical device manufacturers have, by and large, failed to keep pace with modern cyber-attacks.
The requirements and cost of FDA certification make the challenge of building secure devices even harder. But all too often, medical devices have not even included the basic minimum-security features. Only in the past few years have device manufacturers begun to emphasize security for embedded devices, and then only by a few forward looking companies. All too often, security is still an afterthought. Clearly that has to change.
As the MedJack report shows, any insecure medical device can and will be targeted by hackers. Security must become a priority in all phases of medical device development. This will require a significant shift in priorities. New platforms and architectures must be adopted that incorporate security into every level of product design from selection of hardware platforms through application implementation.
Securing Next-Generation Medical Devices
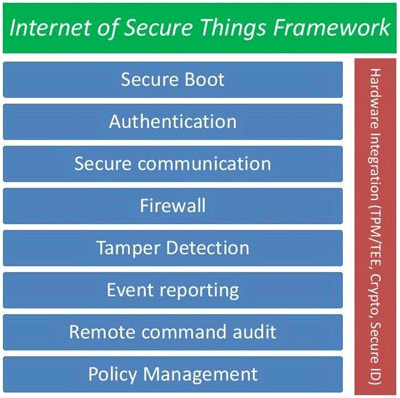
Medical devices need to be designed to include a high level of security within the device. Key features include hardening the device via secure boot, authentication, and intrusion detection. Also important are secure communication (security protocols, embedded firewall), data protection (data in use, data at rest and data in transit), and enabling security management (remote policy management, security event reporting, integration with security management systems).
|
Medical devices require a complete security framework to comply with HIPPA requirements, ensure device protection and avoid being hijacked. |
Securing Legacy Devices
Creating a new generation of highly secure medical devices is critical if we are to ensure future networks and systems are not vulnerable to cyberattacks. But replacing the current installed base of medical devices will take time. There are hundreds of billions of dollars of medical devices in use today and it is not feasible to simply replace this equipment with newer devices.
For those devices that cannot be replace or upgraded, a low cost, bump-in-the-wire (BITW) security device can be used to add a critical layer of protection. It is installed in front of a legacy device and controls all network communication with the device.
Addressing Vulnerabilities
The problems outlined in the MedJack report are not isolated incidents; rather they highlight systemic problems with medical device security. Cybercriminals understand how vulnerable these devices are and actively target medical devices.
Medical device companies must adopt a "security first" approach. Security must be considered a critical requirement starting with a hardware platform that provides security features.
The MedJack report shows how far we still have to go to protect medical data from cybercriminals. If we don't act now, attacks like those outlined in the MedJack report will continue to make headlines.
1. http://www.zakon.org/robert/internet/timeline/
Alan Grau ([email protected]) is the president and co-founder of Icon Labs, a provider of security software for embedded devices. He is the architect of Icon Labs' award winning Floodgate Security Products.
Learn more about medical device security at MEDevice San Diego, September 1-2, 2015. |
Like what you're reading? Subscribe to our daily e-newsletter.
About the Author(s)
You May Also Like